
A Mobile Device Enrollment Program Can Greatly Benefit Businesses
In today's world, where smartphones are the devices of choice for many users, a mobile device enrollment program should be a key part of any MDM rollout.
Get the latest insights from Samsung delivered right to your inbox.
Follow Us
Get the latest insights from Samsung delivered right to your inbox.

In today's world, where smartphones are the devices of choice for many users, a mobile device enrollment program should be a key part of any MDM rollout.

The mobile-first mentality affects every facet of your business. Here's a look at the four segments that can help you achieve application realization.

Mobile enablement is critical to employee productivity because it allows employees to access the right tools in their (and their customers’) moments of need.

An effective mobile security policy must be multilayered and secure both devices and its supporting infrastructure.

Some organizations are concerned about security in BYOD adoption. Enterprise mobility management can keep both corporate and user data secure.
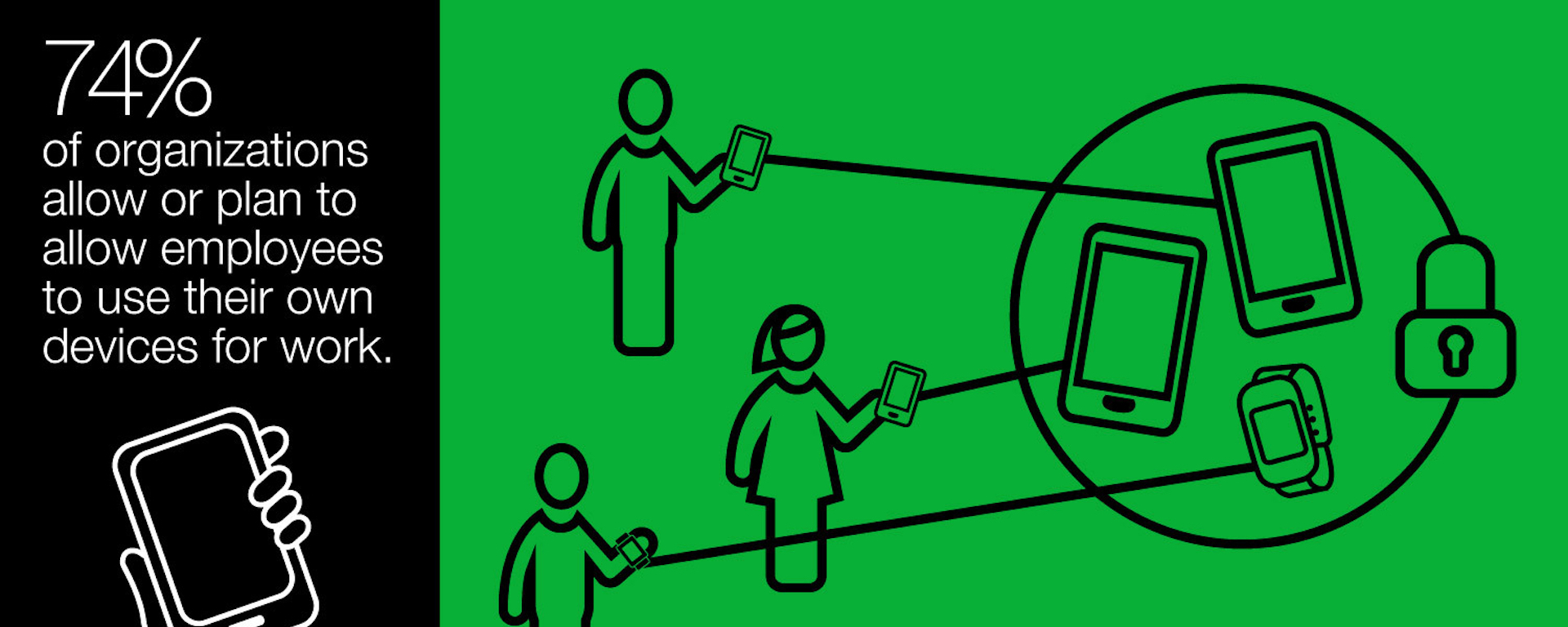
Enterprise mobility management boosts data security while allowing the flexibility and productivity gained from mobile devices.

When organizations deploy enterprise app stores, employees download trusted software that has been vetted for security and that won't leak sensitive data.

Mobile devices create new security needs. If your enterprise mobility management isn't meeting them, it may be time to change providers.

The recent proliferation of mobile devices within enterprises is high atop the list of data and employee security vulnerabilities. A recent PWC survey of

The implementation of bring your own device (BYOD) policies in high-security environments is open for debate, and the enormous benefits related to BYOD must