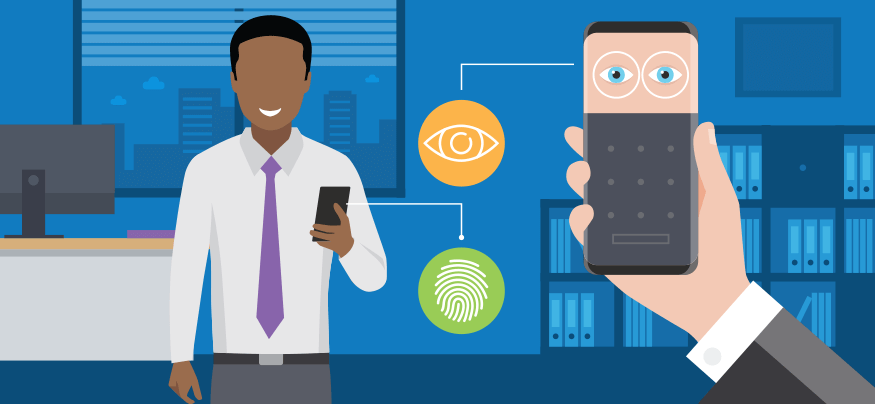
It’s hardly worth mentioning how bad passwords are; IT managers have been hearing that they need to get rid of passwords for, literally, decades. And every breach that begins with “stolen credentials were used to …” just reinforces that message. However, switching away from passwords is easier in the PowerPoints than it is in real life — unless you’re talking about smartphones. Because with smartphones, finally, moving away from simple passwords is easy.
For several years, smartphones have been equipped with specialized hardware to capture biometric data: primarily fingerprints, iris patterns, face patterns and voice recognition. With this hardware, IT managers can quickly and easily switch to biometrics and immediately improve phone security. Additionally, because end users are getting experience with biometric authentication on their personal smartphones, they are more comfortable with the technology, bringing fewer training issues and support calls.
Unlocking Phones and Authenticating Applications
End users are already familiar with the idea of unlocking their smartphones with biometrics, but that’s really just the start. Using technology standardized by the Fast Identity Online (FIDO) Alliance, biometrics can be securely extended to enterprise applications, both in corporate data centers and, in some cases, with cloud-based services.
FIDO provides a way to move from passwords to very secure public-key cryptography for authentication in a simple and standardized way.
When an application is FIDO authentication enabled, the user is essentially authenticating by proving knowledge of the private key in a public/private key pair — the biometrics are simply the way that the private key is unlocked on the user’s FIDO-enabled device, such as a smartphone or tablet.
Having public-key cryptography locked up with biometrics (or other hardware two-factor authentication) means that IT managers don’t have to focus on whether fingerprints are better than iris scans or USB dongles. Once an IT manager pushes FIDO APIs into enterprise applications for authentication or selects cloud-based applications that support FIDO, such as Salesforce.com, Google’s enterprise application suite and Dropbox, users can bring a variety of biometric authentication tools to the table without having to change the application.
Secure Your Employee Phones with Biometrics
Download this practical guide to learn how Samsung Pass keeps mobile data safe. Download Now
IT managers who want to jump on the FIDO bandwagon should look for smartphones that use trusted hardware or Trusted Execution Environments (TEEs) to isolate and protect biometric data from the rest of the phone. Users are understandably concerned with biometric data being stolen — after all, your fingerprints and irises are passwords that you can never change. For maximum user acceptance, a little pro-privacy preparation is helpful. IT managers should be able to assure users that biometrics aren’t being stored, aren’t leaving the smartphone, aren’t being pushed up to the cloud somewhere, and are walled off from any malicious applications that might be running.
Which Biometric Is Best?
The next question that most IT managers will ask is “which biometric is the best?” There is no “one size fits all” answer to this. What is important is providing options, so that IT managers can select the most appropriate technology for their devices and users.
Obviously, one factor is whether the device supports biometrics in the first place. Fingerprints are very popular for this reason, as most smartphones and tablets have fingerprint readers on-board, and are only beginning to offer other technologies.
However, fingerprints aren’t always the best choice. For example, smartphones might be placed in protective cases that don’t let the fingerprint reader function properly. In some environments, such as factory floors or cold weather, end users will be wearing gloves, which block fingerprint recognition.
Smartphones and tablets that have either iris readers or facial recognition are entering the market, but are not a universal solution. For example, if the user base for an application is “people wearing masks,” such as medical staff or someone in a polluted environment, facial recognition won’t work. Eyeglasses don’t usually block iris scanners, but some types of sunglasses will.
While the popular press may be full of stories of various types of biometric authentication failing, IT managers should remember that the plural of anecdote is not data. Generally, enterprises that have tested fingerprint authentication against other types of biometrics find that the false acceptance and false rejection rates for iris scanners and face scanners are lower than for fingerprints; some studies have found dramatically better results.
Addressing Adoption and Security Levels
Another difference in authentication methods is the enrollment effort — the amount of time it takes to capture the reference copy of the user’s biometric data, with fingerprint and voice authentication being seen as more time-consuming and error-prone during the enrollment than old-school passwords.
There are differences in the security level offered by various biometric authentication technologies in smartphones, as well. However, because of the wide variety of hardware used in fingerprint readers — there are a half-dozen different approaches to reading fingerprints in common use — and the small number of iris and facial recognition phones in the marketplace, it’s hard to make general statements about the security of different methods. However, one thing is clear: biometrics overall are much more secure than standard passwords, even with some false positives and false negatives in the mix.
IT managers now have excellent options built into smartphones and tablets for replacing or augmenting passwords to increase information security. With many types of biometrics to handle different types of user communities, there is a strong reason to investigate and implement these technologies.
Get a look how advanced iris scanning can help add biometric security measures to your enterprise.