Companies are always looking for ways to streamline processes and to make employees more efficient. Sometimes this means allowing employees to use their personal smartphones and tablets to do their jobs. In early 2015, Google unveiled Android for Work with the goal of making the Android platform more attractive for business users. The Android for Work program offers a dedicated work profile on any Android tablet and smartphone running the latest version of Android, Lollipop. This ensures that personal and company data remain separate on the devices. According to a 2015 post from Google, more than 100,000 organizations are already using the service, and it’s working with close to 40 partners, including popular device manufacturers, carriers and application developers to expand the appeal and use of Android devices.
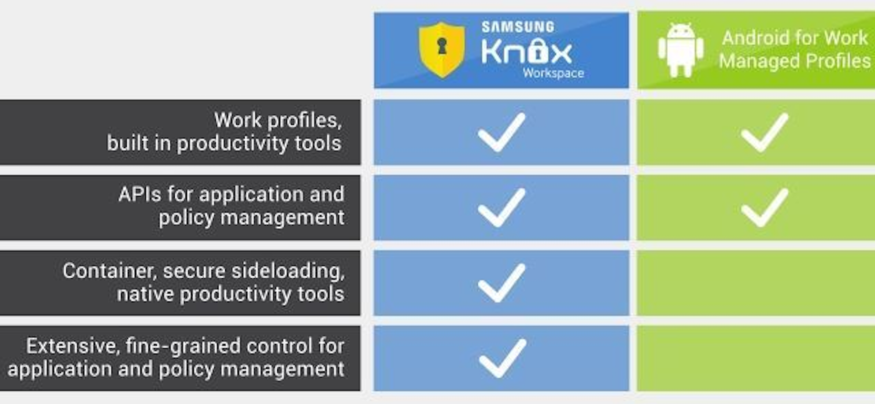
One such partner is Samsung, which gives Android for Work a major competitive advantage: the containerization capabilities of Samsung KNOX. By separating work and personal data on a single device, organizations can enable employees to use their personal devices for work without compromising sensitive company data. The separation of work data into a special container enables policy control at the enterprise level, and it secures the distribution and management of applications. Some work productivity apps are built into the devices and additional apps can be downloaded through official app stores. In addition, KNOX security features such as disk encryption, screen locking and VPN support can be added to devices. IT administrators can monitor and manage settings, apps and data associated with work profiles, as well as network activity for additional security and governance purposes.
By making Android for Work available on its smartphones and tablets, Samsung provides an additional layer of certainty for security-conscious organizations that want assurance that their data security and privacy requirements are being met. Samsung KNOX offers defense-grade security that meets the most stringent security requirements by protecting the integrity of devices from hardware to applications. The KNOX security features on Samsung Galaxy smartphones and Galaxy tablets include embedded platform security, trusted and secure boot, a trusted zone at the kernel level and policy management and enforcement. It also has achieved a range of certifications attesting to the high levels of security offered, including FIPS 140-2, Common Criteria and many others. Thanks to its integration with Samsung KNOX, Android for Work can meet the demands of even the most highly regulated industries, including government agencies, financial institutions and healthcare organizations, where security regulatory requirements are extremely demanding.
Samsung and Google Deliver the Most Secure Android Solution from Samsung Business USA
With the additional KNOX security features, organizations can be sure that user devices are secure right from the moment that they are powered on, providing an extra layer of assurance that sensitive data is safeguarded. Because work and leisure applications and data are stored in and accessed from separate containers on a device, organizations will be better able to embrace BYOD programs and the benefits they offer in the most secure manner. They can ensure that policies are enforced and that sensitive data will not leak out of the organization. By partnering in the Android for Work initiative, Google and Samsung are delivering the most secure Android solution that there is, providing ease of mind for any organization.